Table of Contents |
Transmission Control Protocol/Internet Protocol (TCP/IP) is a standard for computer network communication, used for the internet and most other modern networks as well. TCP/IP was originally developed by the Internet Engineering Task Force (IETF), which is a standards organization for the internet responsible for the technical standards that comprise the TCP/IP protocol suite. TCP/IP is a suite of protocols that operate at Layers 3, 4, and 7 of the OSI model.
TCP/IP maps to a U.S. Department of Defense (DoD) model that is similar to the OSI model. The DoD model is composed of four layers instead of seven:
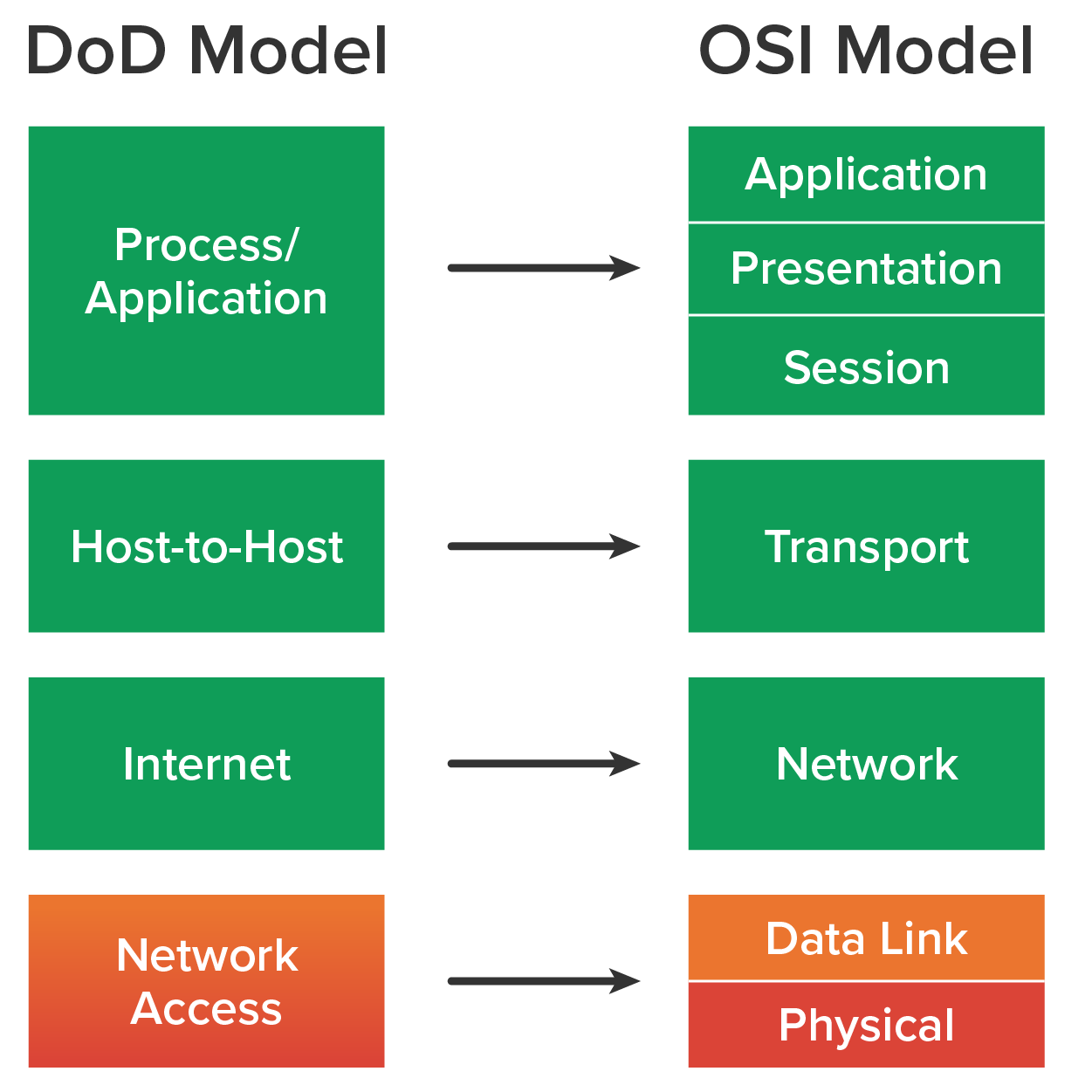
A vast array of protocols operate at the DoD model’s process/application layer to integrate the various activities and duties that are the focus of the OSI’s corresponding top three layers (application, presentation, and session). The process/application layer defines protocols for node-to-node application communication and also controls user interface specifications.
The host-to-host layer parallels the functions of the OSI’s transport layer, defining protocols for setting up the level of transmission service for applications. It tackles issues such as creating reliable end-to-end communication and ensuring the error-free delivery of data. It handles packet sequencing and maintains data integrity.
The internet layer corresponds to the OSI’s network layer, which designates the protocols related to the logical transmission of packets over the entire network. It takes care of the logical addressing of hosts by giving them an IP address, and it handles the routing of packets among multiple networks.
At the bottom of the DoD model, the network access layer monitors the data exchange between the host and the network. The network access layer, the equivalent of the data link and physical layers of the OSI model, oversees hardware addressing and defines protocols for the physical transmission of data.
The DoD and OSI models are similar in design and concept and have similar functions in similar layers. The diagram below shows the TCP/IP protocol suite and how its protocols relate to the DoD model layers.
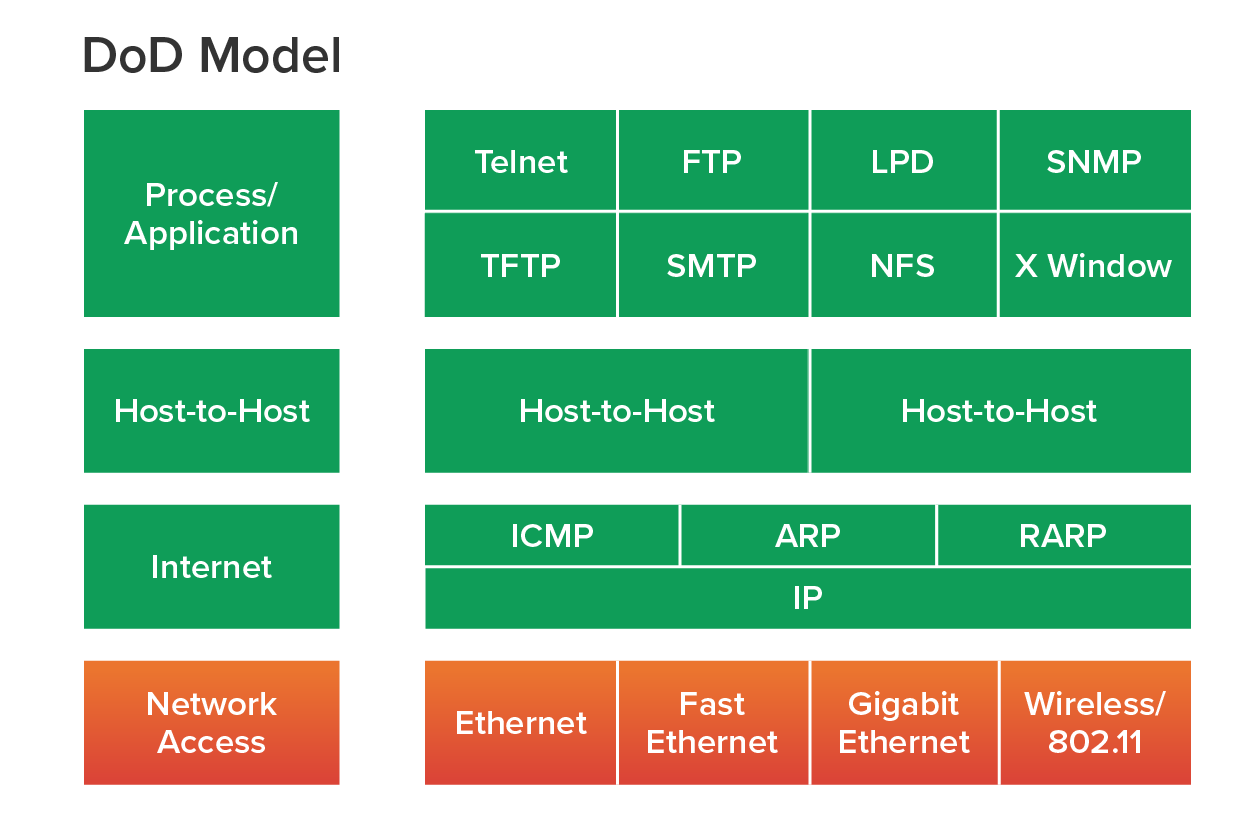
We will now look at various TCP/IP protocols in more detail, starting with the application layer protocols. You likely use many of these every day, while others are used primarily by information technologists who manage networks.
In the following sections, we will describe the different applications and services typically used in IP networks and list their associated TCP or User Datagram Protocol (UDP) port numbers as well.
Telnet (TCP 23) supports terminal emulation. It allows a user on a remote client machine to access the resources of another machine, the Telnet server. Telnet enables the client machine to appear as though it were a terminal directly attached to the local network. Telnet offers no security or encryption and is a legacy protocol that has been replaced by Secure Shell (SSH).
File Transfer Protocol (FTP), (TCP 20, 21) is the protocol that lets you transfer files across an IP network, and it can accomplish this between any two machines that are using it. One common use of FTP is to use it to upload a revised website file to a web server.
Secure File Transfer Protocol (TCP 22)is used to transfer files over an encrypted connection. It uses an SSH session, which encrypts the connection; SSH uses port 22, hence the port number 22 for SFTP.
Trivial File Transfer Protocol (TFTP), (UDP 69) is a connectionless version of FTP that uses UDP instead of TCP at Layer 4, so there is no guarantee of delivery.
Simple Mail Transfer Protocol (SMTP), (TCP 25) enables the transfer of emails from email server to email server. It does not offer a server-to-client email service. SMTP carries, for example, email messages from a Gmail server to an Apple email server. Once delivered to either server, your login credentials for your server will allow you to access the message from the email client you use to access your email account.
Post Office Protocol (POP), (TCP 110)enables email transfer between an email server and an email client for client-side storage. When a client device connects to a POP3 server, messages addressed to that client are released for download.
Internet Message Access Protocol (IMAP), Version 4 (TCP 143)enables email transfer between an email server and an email client for server-side storage. IMAP supports search commands used to look for messages based on their subject, header, or content. IMAP supports Kerberos authentication for security. IMAP is the protocol that your current email service uses to send messages to your computer.
Remote Desktop Protocol (RDP), (TCP 3389) is a protocol that allows you to connect to another computer and run programs. Clients exist for most versions of Windows, and Macs now come with a preinstalled RDP client.
Both Transport Layer Security (TLS) and its forerunner, Secure Sockets Layer (SSL), are cryptographic protocols for enabling secure online data transfer activities. Both use cryptography to authenticate the host they are communicating with and to exchange a key. This key is then used to encrypt data flowing between the hosts, which allows for data/message confidentiality, message integrity, and message authentication.
Session Initiation Protocol (SIP) is a signaling protocol used to enable multimedia communication sessions for many aspects like voice and video calls, videoconferencing, streaming multimedia distribution, instant messaging, presence information, and online games over the internet.
Real-Time Transport Protocol (RTP) (UDP 5004/TCP 5005) describes a packet-formatting standard for delivering audio and video over the internet. It is commonly employed for streaming media, videoconferencing, and Voice over Internet Protocol (VoIP).
Media Gateway Control Protocol (MGCP) (TCP 2427/2727) is a standard protocol for handling the signaling and session management needed during a multimedia conference with multiple participants. The protocol defines a means of communication between a media gateway, which converts data from the format required for a circuit-switched network to that required for a packet-switched network, and the media gateway controller.
H.323 (TCP 1720) is a protocol that provides a standard for video on an IP network that defines how real-time audio, video, and data information are transmitted. This standard provides signaling, multimedia, and bandwidth control mechanisms. H.323 uses the RTP standard for communication.
Simple Network Management Protocol (SNMP), (UDP 161) collects and manipulates valuable network information from network devices like routers and switches. It gathers data by polling the devices on the network from a management station at fixed or random intervals, requiring them to disclose certain information. The network uses agents, and when problems occur, the agents send an alert called a trap to the management station. SNMP enables the administration of a network.
Secure Shell (SSH), (TCP 22) protocol sets up a secure encrypted Telnet session over a standard TCP/IP connection and is used to securely log in to other systems, run programs on remote systems, and move files from one system to another.
Hypertext Transfer Protocol (HTTP), (TCP 80) is used to manage communications between web browsers and web servers, and it opens the right resource when you click a link, wherever that resource may reside. HTTP is the protocol that delivers webpages to your browser.
Hypertext Transfer Protocol Secure (HTTPS), (TCP 443) is an encrypted version of HTTP that has security tools for keeping transactions between a web browser and a server secure. It is what your browser needs to fill out forms, sign in, authenticate, and encrypt an HTTP message when you make a reservation or buy something online.
Network Time Protocol (NTP), (UDP 123) works to ensure that all the computers on a given network are set to the same time. This is important because many of the transactions done today are time stamped and date stamped.
Lightweight Directory Access Protocol (LDAP), (TCP 389)enables access to computer directories. Its third version is most commonly used today and is described in RFC 3377.
Internet Group Management Protocol (IGMP) is the TCP/IP used for managing IP multicast sessions. IGMP messages support active multicast streams. IGMP works at the network layer and does not use port numbers.
Network Basic Input/Output System (NetBIOS) and (UDP 137–139) provides an interface for separate computers running Windows to communicate over a network.
Server Message Block (SMB), (TCP 445) is used for sharing access to files and printers and other communications between hosts on a Microsoft Windows network.
Domain Name Service (DNS), (TCP and UDP 53) resolves hostnames to their corresponding IP addresses. DNS allows you to use a domain name to specify an IP address.
Source: This content and supplemental material has been adapted from CompTIA Network+ Study Guide: Exam N10-007, 4th Edition. Source Lammle: CompTIA Network+ Study Guide: Exam N10-007, 4th Edition - Instructor Companion Site (wiley.com)