Table of Contents |
Attackers who break into networks often leave clues behind that can help you sleuth out their identities as well as how they gained access. A great tool for doing network detective work is known as an intrusion detection system (IDS).
Firewalls are designed to block unauthorized traffic from entering your network, but an IDS is more of an auditing tool; it keeps track of all activity on your network so you can see if someone has been trespassing. Because the technology behind IDSes is fairly new, people are busy developing ways to combine IDS technology with existing firewalls.
There are two kinds of IDSs that can detect attacks or intrusions. The first, often referred to as a misuse-detection IDS (MD-IDS), is based on the signature of an intrusion, and it works by looking for fingerprints, which in this case means strange or abusive use of the network. The IDS sends up an alarm only if it recognizes the fingerprints typical of attackers.
The second approach looks for anomalies in network activity, or an anomaly-detection IDS (AD-IDS). An AD-IDS basically watches for anything out of the ordinary; if it discovers fingerprints where there should not be any, it will send out an alert.
The diagram below shows an MD-IDS in action.
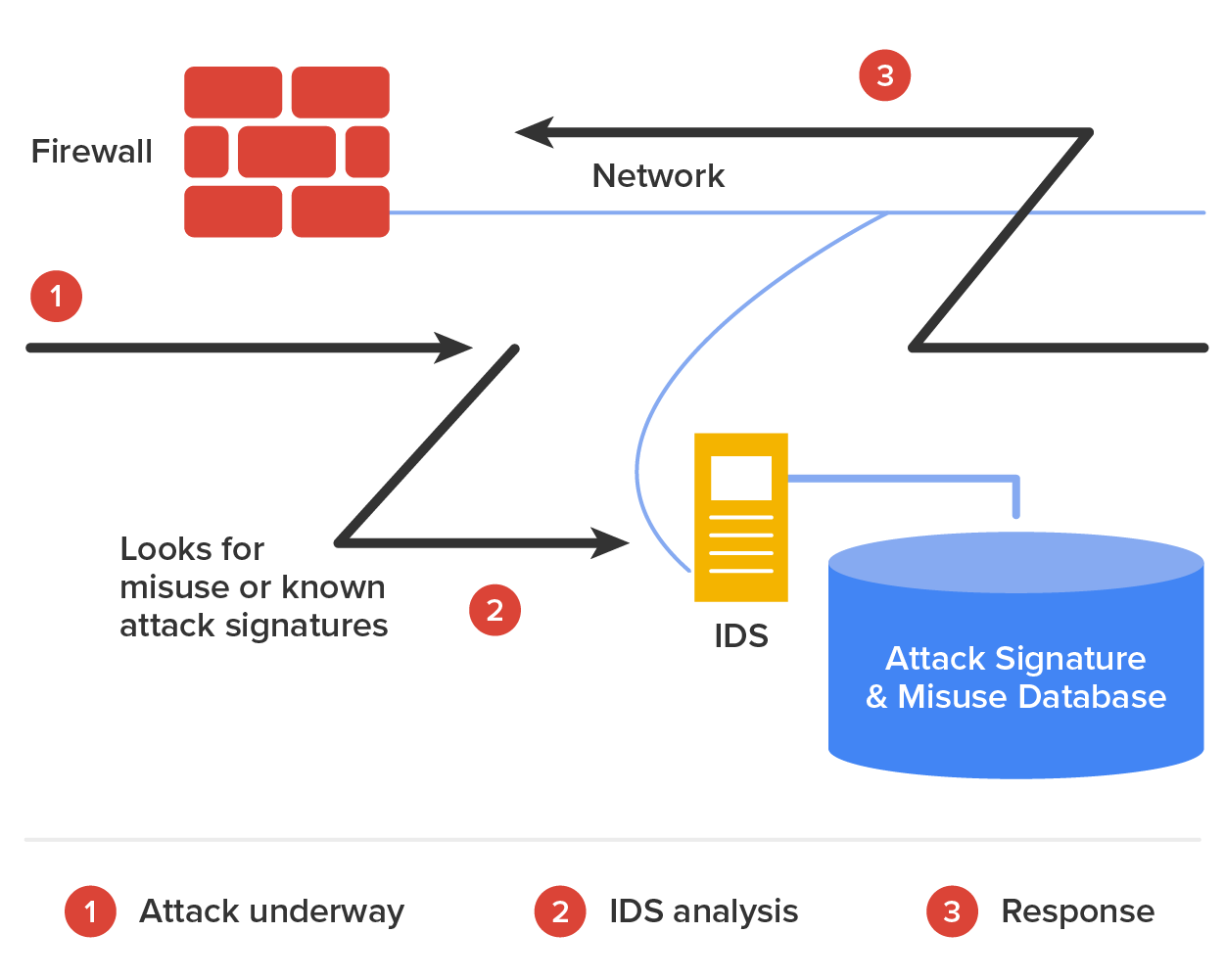
An IDS is a system made up of several components, including one or more sensors to detect events, a console to control and configure the sensors and monitor events, and a database that records the events. These three elements can all be on the same device, or they can be implemented on multiple devices.
The two most common types of IDS implementations are network-based and host-based.
The most common implementation of a detection system is a network-based IDS (NIDS), where the IDS is a separate device attached to the network via a machine like a switch or directly via a tap. Some IDSes are even capable of attaching to the network both outside and inside the firewall; this gives you the best security because you can see what is happening outside of your network and learn to recognize exactly what’s getting through your defenses. The diagram below gives you an example of what a typical IDS setup can look like.
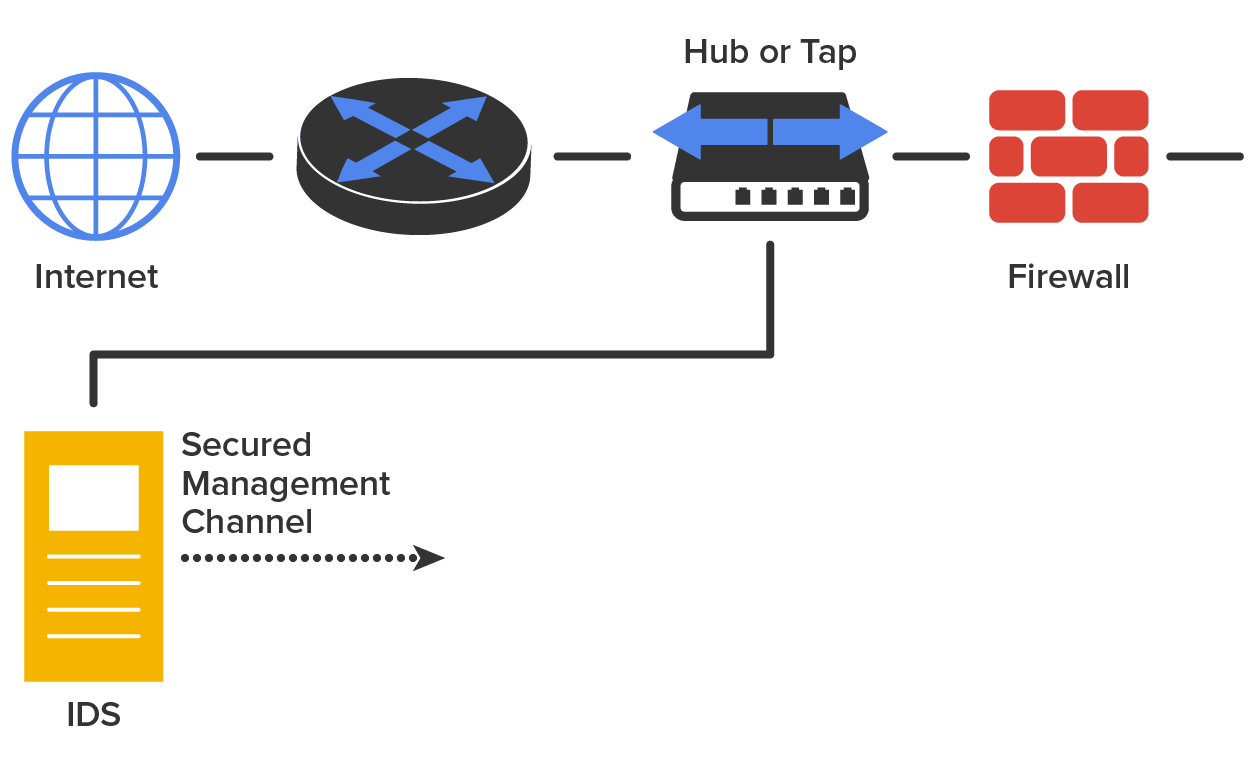
In a host-based IDS (HIDS), software runs on one computer to detect abnormalities on that system alone by monitoring applications, system logs, and event logs, and not by directly monitoring network traffic.
Active responses mean taking immediate action. When an IDS moves to prevent an attack, it’s often called a reactive system or an intrusion protection system (IPS). Here are three common active responses:
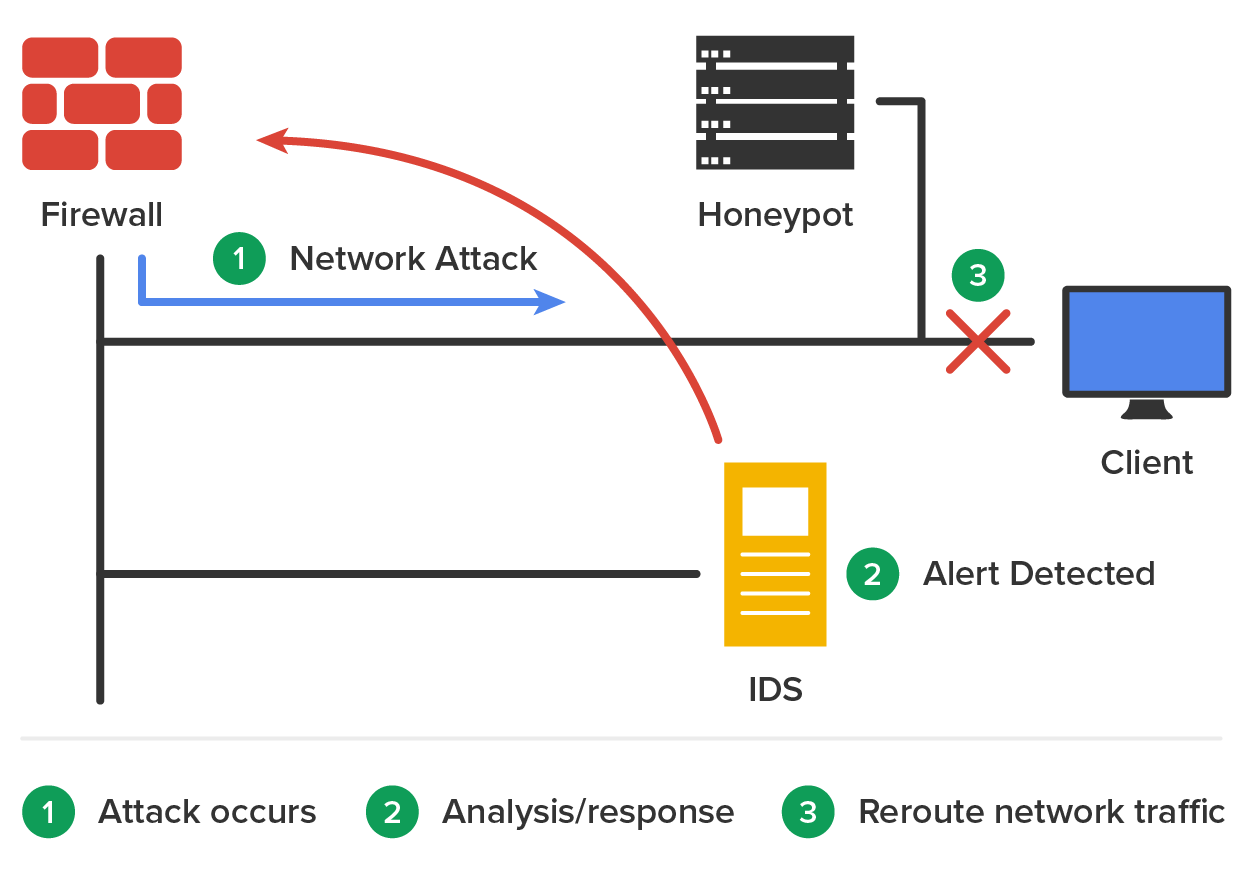
One of the most effective ways to determine if security holes exist in the network is to think like an attacker and attack your own network. Penetration testers often use the same tools that the hacker might use to identify network weaknesses.
EXAMPLE
If we wanted to verify the proper application of some ACLs to a firewall, we could do so with scanning services supplied by a vulnerability scanner. In the following sections, we will cover two of the most widely known and effective programs that can be used for this purpose.IN CONTEXT
Nessus is a proprietary vulnerability scanning program that requires a license to use commercially yet is the single most popular scanning program in use. It normally is executed from the command line because it can thus be included in batch files that can automate its operation on a schedule. Its output can be reported in a variety of formats, including plain text, HTML, and XML.
It operates by performing a port scan and then follows up with more specific tests and scans based on the ports open. It can identify a wide array of weaknesses, including the following:It can also perform an active attack such as denial of service or a dictionary attack.
- Unsecured access to sensitive data on a system
- Misconfigurations like open mail relay and missing patches
- Password issues such as the use of default passwords, common passwords, and blank passwords on system accounts
Network Mapper (Nmap) was originally intended to simply identify devices on the network for the purpose of creating a network diagram. Its functionality has evolved, however, and now it can also do the following:
Unified threat management (UTM) devices perform multiple security functions within the same appliance:
A VPN concentrator is a device that creates remote access for virtual private networks (VPNs) either for users logging in remotely or for a large site-to-site VPN. In contrast to standard remote-access connections, remote-access VPNs often allow higher data throughput and provide encryption. Large enterprises may use concentrators that support anywhere from 100 users up to 10,000 simultaneous remote-access connections.
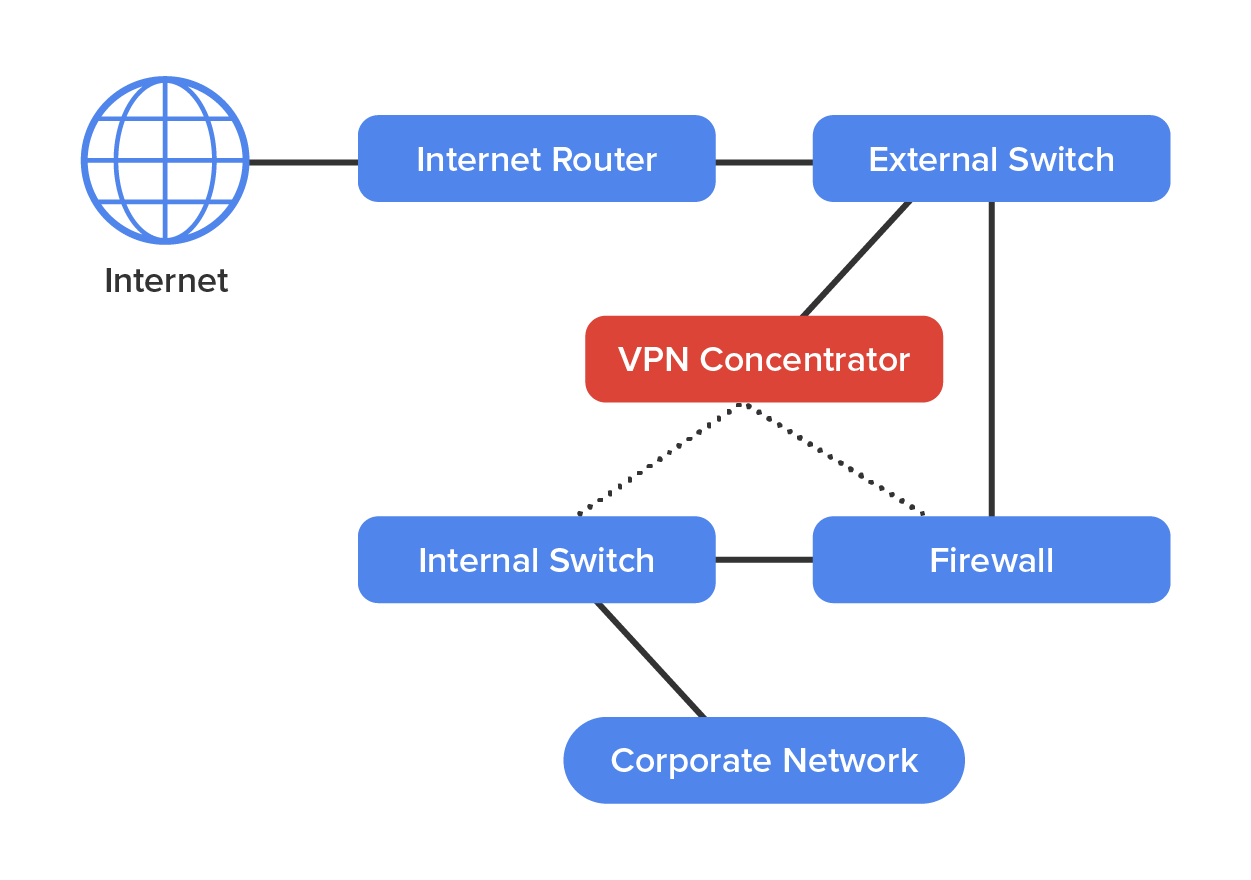
Encryption for a remote-access VPN through a concentrator is usually handled by Internet Protocol Security (IPSec) or by Secure Sockets Layer (SSL), and user authentication can be achieved via Microsoft’s Active Directory, Kerberos, Remote Authentication Dial In User Service (RADIUS), Rivest, Shamir, and Adleman (RSA), and digital certificates. Many VPN concentrators also have a built-in authentication server and allow ACLs to be implemented through them. In the diagram above you can see where VPN concentrators are usually placed within a network setup.
Source: This content and supplemental material has been adapted from CompTIA Network+ Study Guide: Exam N10-007, 4th Edition. Source Lammle: CompTIA Network+ Study Guide: Exam N10-007, 4th Edition - Instructor Companion Site (wiley.com)