Table of Contents |
Professional tone in email includes your subject lines, greetings, and signatures. These elements create first and last impressions. They establish credibility and help recipients understand your message's purpose.
The table below shows how to write effective subject lines, greetings, and signatures to maintain a clear, professional tone in every email.
| Element | Best Practices | What to Avoid | Examples |
|---|---|---|---|
| Subject lines |
|
|
✔ “Budget approval needed by Friday” ✔ “Action required: Submit report by Wednesday” ✘ “HEY!!!” |
| Greetings |
|
|
✔ “Dear Mr. Ahmed” ✔ “Hi Ciara” ✔ “Good morning, team” ✘ “Hey” |
| Signatures |
|
|
✔ Jane Smith, Marketing Coordinator, XYZ Corporation ✘ Large logos, inspirational quotes |
The way you format an email makes a big difference in how it is received. The image below compares a poorly formatted email with a professionally written one to show how tone, structure, and clarity can impact workplace communication.
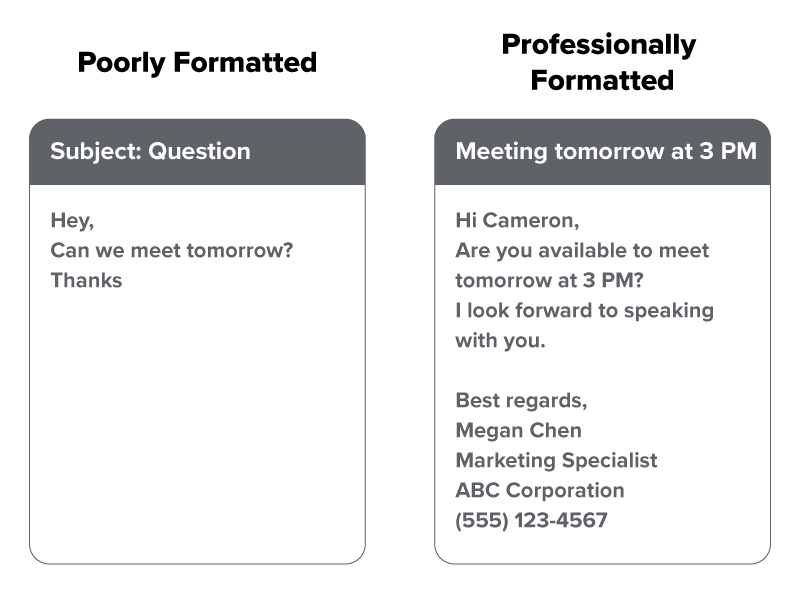
Clear, thoughtful writing shows that you respect your reader and increases the chances of getting a timely, helpful response.
Beyond tone and structure, email platforms offer built-in tools like reply options, formatting, and attachments. Knowing how and when to use these features helps you communicate clearly and avoid common mistakes. These features also protect privacy when used correctly.
Email platforms include options like CC (Carbon Copy) and BCC (Blind Carbon Copy) that help you manage who receives your message. The table below explains when to use each and what to avoid.
| Option | When to Use | What to Avoid |
|---|---|---|
| CC | When others need to be informed or kept in the loop (e.g., supervisors or team members). Everyone included can see who else received the email. | CCing people who do not need the information—it adds unnecessary emails to their inbox and creates clutter and confusion |
| BCC | To send the same message to multiple people without sharing their email addresses. This protects privacy, especially with large or external groups. | Using BCC when recipients expect to see who else received the message—this can create confusion or reduce transparency |
IN CONTEXT: Sharing Information While Respecting Privacy
You are organizing a volunteer event and need to send details to your team and some outside partners.
You CC your supervisor and a few teammates so they can stay informed and see who is involved. Everyone on the CC list can view the same message and each other’s email addresses.
You also need to send the same information to 15 community partners. To protect their privacy, you BCC them—this way, they will not see each other’s contact information.
If you had used CC instead, you would have accidentally shared their email addresses with the whole group, which is not appropriate for outside contacts.
In addition to choosing who gets your message, it is also important to respond appropriately. Knowing when to use Reply or Reply All helps avoid confusion and unnecessary emails. The table below shows the difference between Reply and Reply All
| Option | When to Use | What to Avoid |
|---|---|---|
| Reply | When your response is only for the sender—helps keep the conversation focused and avoids extra emails | Replying to everyone unless your response is relevant to all |
| Reply All | When everyone on the original message needs to see your reply (e.g., confirming attendance, team updates) | Replying to all when your message is meant for one person—always check the recipient list first |
EXAMPLE
You confirm a team meeting by clicking “Reply All” so everyone knows you will attend, but later you send a private question to the organizer using “Reply” to avoid cluttering the group thread.Sometimes, you may be unavailable for extended periods. In those cases, setting an auto reply helps manage expectations and keeps communication professional.
A well-written auto reply lets others know when you will be back and who to contact if something is urgent. Use the guidelines below to write a clear and helpful message.
Mastering these tools also builds confidence. When you know how to use features like CC, BCC, Reply All, and auto replies correctly, you can focus more on your message and less on worrying whether you sent it the right way.

Using email in the workplace involves more than writing clearly—it also means protecting your information and avoiding common security risks.
You were introduced to phishing in Tutorial 1.1.4: Digital Hygiene. Phishing means fake emails that try to steal your personal information.
It is important to revisit phishing here, along with other common email threats:
| Threat | What to Watch For | What to Do | Example |
|---|---|---|---|
| Phishing |
|
|
An email that says “Your account is locked—click here to reset your password now” from a strange-looking address |
| Suspicious links |
|
|
A link that says "paypal.com" but actually leads to “paypalsecurity-alerts.xyz” |
| Unsafe attachments |
|
|
A file attached to a vague message like “Open this file immediately” from an unknown sender |
Source: THIS TUTORIAL HAS BEEN ADAPTED FROM THE NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY’S “TRUSTWORTHY EMAIL (SPECIAL PUBLICATION 800-177 REV. 1).” ACCESS FOR FREE AT CSRC.NIST.GOV/PUBS/SP/800/177/R1/FINAL. CONTENT IS IN THE PUBLIC DOMAIN. USE DOES NOT IMPLY ENDORSEMENT BY NIST OR THE U.S. GOVERNMENT.
REFERENCES
Herrity, J. (2025, June 7). 28 email etiquette rules for the workplace. Indeed. www.indeed.com/career-advice/career-development/email-etiquette
Rose, S., Nightingale, J., Garfinkel, S., & Chandramouli, R. (2019). Trustworthy email (NIST Special Publication 800-177 Rev. 1). National Institute of Standards and Technology. csrc.nist.gov/pubs/sp/800/177/r1/final
University of Virginia. (n.d.). Examples of phishing and scam emails. Information Security. security.virginia.edu/examples-phishing