Table of Contents |
In today’s world, we expect to be always connected, whether we’re having a meeting online, sending a direct message (DM), or searching something random like “do fish blink?” Behind this everyday convenience lies a vast, often invisible system: networks that link computers and devices so that they can share information and resources. Much of this connectivity depends on physical infrastructure, specifically, over a million miles of underwater cables that stretch across oceans to carry the world’s internet traffic. The map below shows just how extensive this network is. These networks form the backbone of nearly everything we do online, whether they run through underwater cables, span wirelessly across countries, or connect devices within homes and businesses, enabling everything from streaming music to running entire companies.
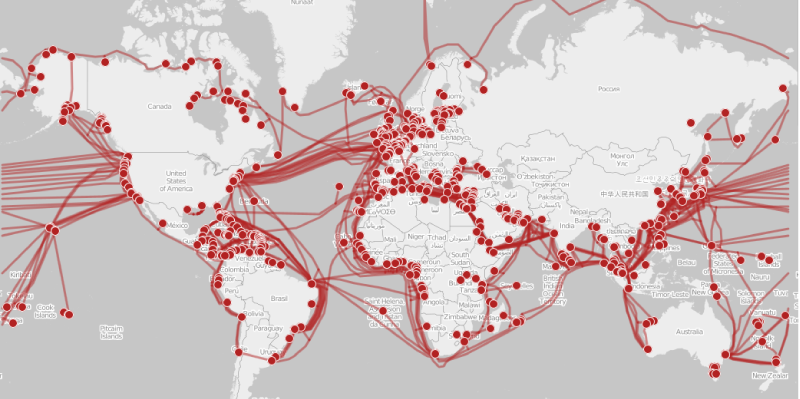
For a network to function well, it must be both reliable and secure. Think back to the childhood game of telephone. As a message passed from person to person, it often became distorted or didn’t reach the final person at all. If modern networks worked that way, digital communication would be confusing or impossible. A reliable network ensures that information travels smoothly between devices without delays or loss. A secure network ensures that the information reaches only the right people and is protected from unauthorized access, theft, or interference.
Supporting these two goals, reliability and security, are two major areas of IT: networking and cybersecurity. Network professionals design and maintain the systems that keep devices connected and data flowing efficiently. Cybersecurity professionals focus on identifying risks, defending against attacks, and keeping systems and data safe from unauthorized access. These fields are closely connected, and many IT professionals work across teams to support both the performance and protection of modern networks.
There are many career paths within each area. In networking, roles include network administrators, network architects, and cloud networking specialists. In cybersecurity, professionals may become penetration testers, security engineers, or compliance analysts. In this lesson, you will explore these career fields by focusing on two key roles: the network engineer, who helps build and manage reliable systems, and the cybersecurity analyst, who works to secure them from threats. By comparing these roles, you will gain insight into how networking and security professionals work together to support the digital systems we all rely on.
Networking professionals are responsible for keeping devices, systems, and people connected. Their work ensures that data moves smoothly, securely, and reliably between computers and across networks. These professionals handle the design, maintenance, and performance of network systems used in everything from small offices to large-scale enterprise environments.
Within the field of networking, professionals take on different roles to support the design, maintenance, and security of network infrastructure, meaning the cables, devices, and systems that make up a functioning network. Network engineers design and build the physical and logical layout of networks, creating the systems that support communication across devices and locations. Network administrators manage and maintain those systems on a day-to-day basis, monitoring network performance and responding to issues. Network security specialists focus on protecting the network from threats and unauthorized access, while some professionals specialize in wireless networking, ensuring smooth connectivity across mobile and wireless devices. Although each role has a unique focus, the roles often overlap in practice and require collaboration to keep networks efficient, secure, and responsive to organizational needs.
Network engineers are responsible for building and setting up systems that allow computers and devices to connect and share information. These systems make everyday tasks such as sending emails, accessing websites, and sharing files possible, whether at home or in the workplace. Network engineers install and configure hardware such as routers, switches, and network cables, which are the physical components of a network. They also plan how information moves through these systems to make sure everything works together.
Part of a network engineer’s job is to make sure that the network can handle the needs of the people using it. This includes thinking about how many devices will be connected, how much speed is needed, and how to keep the network running even if one part of it fails. They design networks that are reliable, fast, and flexible enough to grow as an organization adds more users or services.
While network engineers’ main focus is planning and building networks, they may also help troubleshoot problems, especially when issues affect performance or network design. They use tools to test how the network is running and to adjust it when needed. This role combines problem solving with long-term planning. Network engineers help create systems that keep people and organizations connected; this makes their work essential in almost every field that relies on technology.
Network administrators are responsible for keeping computer networks running smoothly day to day. While network engineers focus on building and setting up networks, network administrators manage and support those systems after they’re in place. Their job is to make sure everything continues to work correctly for the people using it.
A big part of this role involves monitoring network performance. Network administrators check for slow connections, outages, or unusual activity that might affect access to the internet or its speed. When something goes wrong, such as when users can’t connect to a shared folder or the internet is down, they step in to troubleshoot the issue. They also perform routine maintenance, such as installing updates, backing up files, and keeping documentation up to date.
In addition to fixing problems, network administrators help prevent them. They manage user accounts and permissions, maintain firewalls and antivirus tools, and make sure that only authorized users can access certain parts of the network. This role is hands-on, technical, and focused on keeping things running smoothly behind the scenes. Network administrators are often the go-to problem solvers for IT-related issues, and their work helps employees stay connected and productive.
Network security specialists focus on protecting computer networks from threats such as hackers, viruses, and data breaches. Their job is to make sure that only the right people can access the network and that the information moving through it stays safe and secure.
These professionals work with tools such as firewalls, antivirus software, and encryption systems to block unwanted access and detect suspicious activity. They regularly monitor the network to look for signs of attacks or weaknesses and take action to prevent problems before they happen. If a security issue does occur, they investigate the cause and help fix it quickly.
Network security specialists also set rules for how data should be handled and who can access what. They might create policies for strong passwords, train staff on safe internet practices, or respond to alerts about unauthorized access attempts. In some companies, they also ensure that networks comply with government or industry regulations that set specific security standards.
This role is important in any organization that handles sensitive data, such as schools, hospitals, banks, or businesses. Network security specialists help protect not just information but also the people and systems that depend on it. While network security specialists focus on protecting the network itself, other cybersecurity roles handle broader threats across systems, data, and software.
Cybersecurity is about more than just stopping viruses and other digital threats. It involves predicting possible threats, monitoring for suspicious activity, responding to security incidents, and helping organizations prevent future attacks. In this field, different roles focus on different parts of digital security. Some professionals, such as cybersecurity analysts, monitor systems and respond to alerts. Others, such as security operations center (SOC) analysts, work in dedicated security centers to track threats around the clock. Still others, such as penetration testers, take an offensive approach by safely testing systems for weaknesses before real attackers can find them. Cybersecurity roles are in high demand across almost every industry. From banks and hospitals to schools and government agencies, organizations need people who can help protect sensitive information and keep systems secure. Although these roles have different responsibilities, they often work together to prevent, detect, and respond to cyberattacks.
Cybersecurity analysts help organizations stay ahead of potential cyber threats. Their work is focused on prevention and long-term protection. These professionals monitor systems and networks for unusual activities, investigate alerts, and help identify security risks before they turn into major problems.
In addition to analyzing threats, cybersecurity analysts are often responsible for updating firewalls, reviewing security logs, setting access controls, and creating or enforcing cybersecurity policies. They play a key role in strengthening system defenses by recommending software updates, tools, or best practices to reduce risk. For example, they might notice repeated failed logins from unusual locations and investigate whether someone is trying to gain unauthorized access to the system.
Cybersecurity analysts often collaborate with network teams, managers, and end users to raise awareness about common threats such as phishing emails or weak passwords. Their role requires critical thinking, strong communication skills, and up-to-date knowledge of security trends and tools. The role is also one of the fastest-growing careers in IT, with opportunities across nearly every industry.
While cybersecurity analysts focus on identifying risks and improving long-term security strategies, SOC analysts are responsible for real-time monitoring and rapid response. They are often the first to spot suspicious activity and act quickly to contain potential threats. Working in a centralized team known as the security operations center as seen below, SOC analysts use specialized tools to keep an eye on the health and safety of the organization’s digital environment. They review real-time alerts from firewalls, antivirus software, and intrusion detection systems. When something looks off, they investigate further to see whether it’s just unusual behavior or a possible cyberattack.

SOC analysts play a critical role in the early stages of incident response. If a threat is confirmed, they may take steps to contain it, such as disabling an account or isolating a device. Additionally, a key part of their job is documentation of what happened so that the team can learn from the event and improve its defenses.
This role requires strong attention to detail, good communication skills, and the ability to stay calm under pressure. SOC analysts often work in shifts to provide 24-7 security monitoring, especially in large companies, hospitals, government agencies, or financial institutions.
While cybersecurity analysts and SOC analysts focus on detecting and responding to events as they happen, penetration testers, also known as ethical hackers, are cybersecurity professionals who are hired to break into systems. Their job is to simulate cyberattacks to uncover weaknesses before real hackers can find and exploit them.
Penetration testers use the same tools and techniques as cybercriminals, but their goal is to help organizations improve security. They might attempt to gain unauthorized access to networks, steal simulated data, or bypass security controls as part of their testing. After completing the test, they provide detailed reports explaining how they got in and what can be done to close the security gaps.
Their work is often project-based, with each test tailored to a specific system or scenario. This role requires strong technical skills, creativity, and up-to-date knowledge of current threats and hacking methods.
In the workplace, network and cybersecurity professionals often work side by side, but with different priorities. Network professionals focus on keeping systems running smoothly. They make sure that data flows quickly, reliably, and without interruptions. Cybersecurity professionals, on the other hand, focus on keeping that same data and the systems that move it safe from threats.
While their goals differ, their work often overlaps. For example, both teams may use tools such as firewalls, which are security systems that filter network traffic to prevent unauthorized access. They may also rely on virtual private networks (VPNs), which create secure, encrypted connections for users working remotely or transferring sensitive data. Another shared tool is a network monitoring system, which tracks how data moves through the system and alerts staff if anything unusual is detected.
EXAMPLE
Imagine a hospital installing a new wireless network for staff and patient services. Network engineers focus on making sure that Wi-Fi coverage is strong and fast across every floor. At the same time, cybersecurity professionals review the setup to ensure that patient data is encrypted and access to medical systems is restricted. Together, they create a system that is both efficient and secure, which is essential in environments where lives may depend on it.Both roles are essential for a secure and functional IT environment. Without reliable networks, employees cannot access the systems they need. Without security, those same systems are vulnerable to attack. That is why collaboration is key.
Successful organizations encourage strong communication between these teams. Network professionals need to know when security changes might affect how data moves through the system. Security professionals rely on network insights to spot and respond to unusual activities. Working together ensures that neither performance nor protection is compromised.
Source: THIS TUTORIAL WAS AUTHORED BY SOPHIA LEARNING. PLEASE SEE OUR TERMS OF USE.